

J|Down - next item K|Up - previous item Right - next page Left - previous page <Return> - jump to page from toc O - toggle outline mode T|escape|F5 - toogle display of toc S|. - rotate between styles
What's this "Web 2.0" thing anyway?
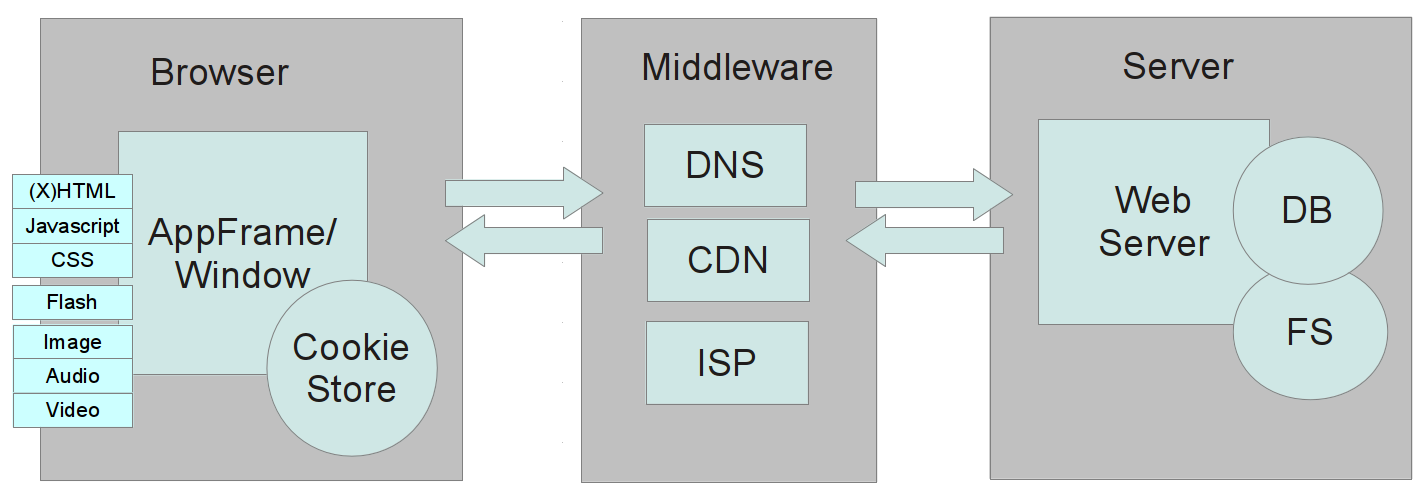
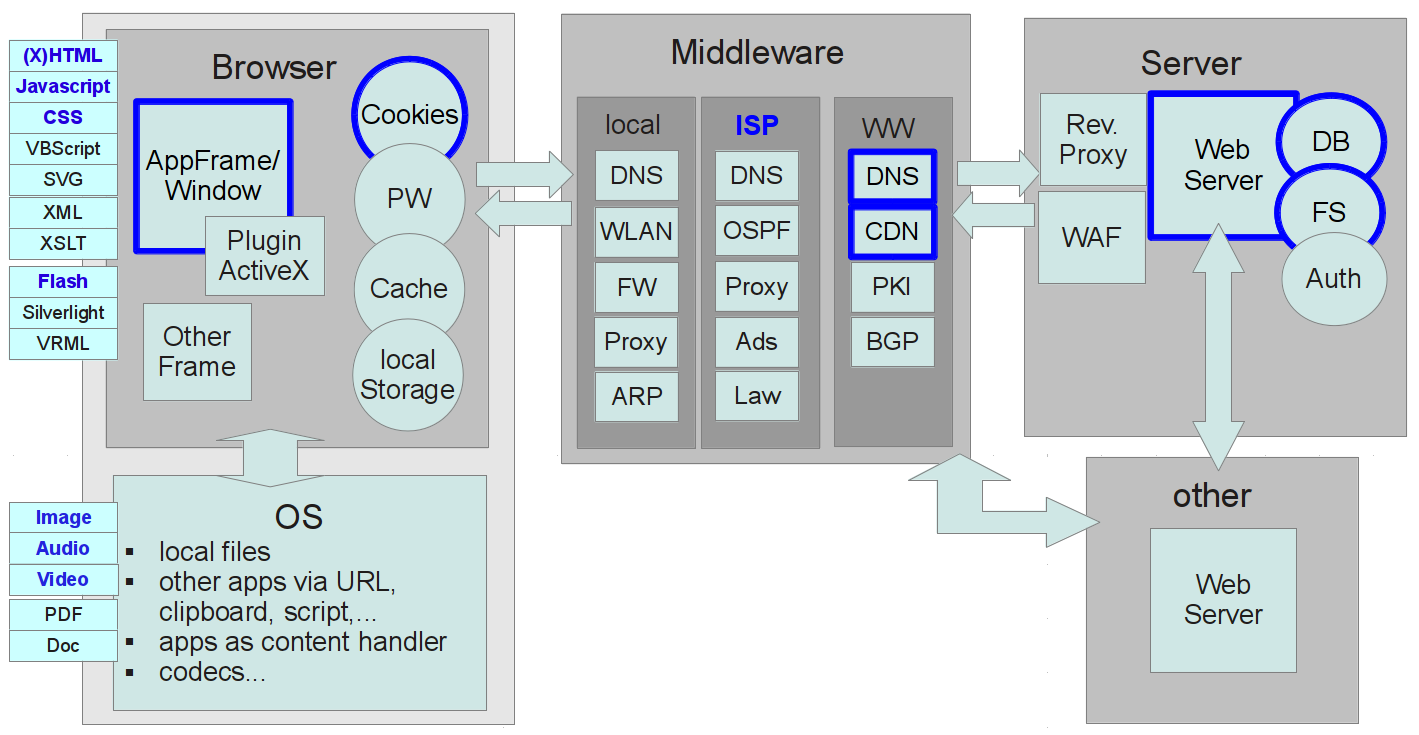
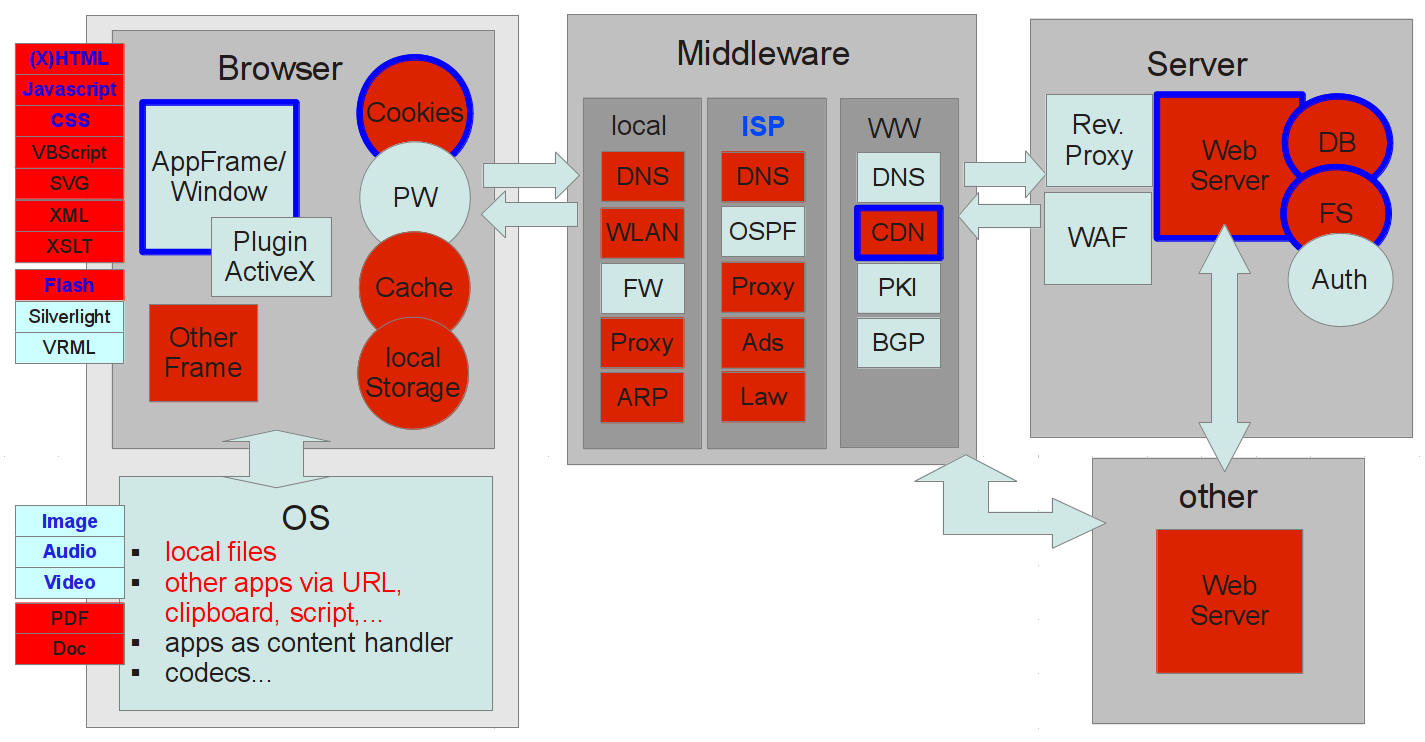
Targets and Methods of the Attacker
SQL Injection
XSS
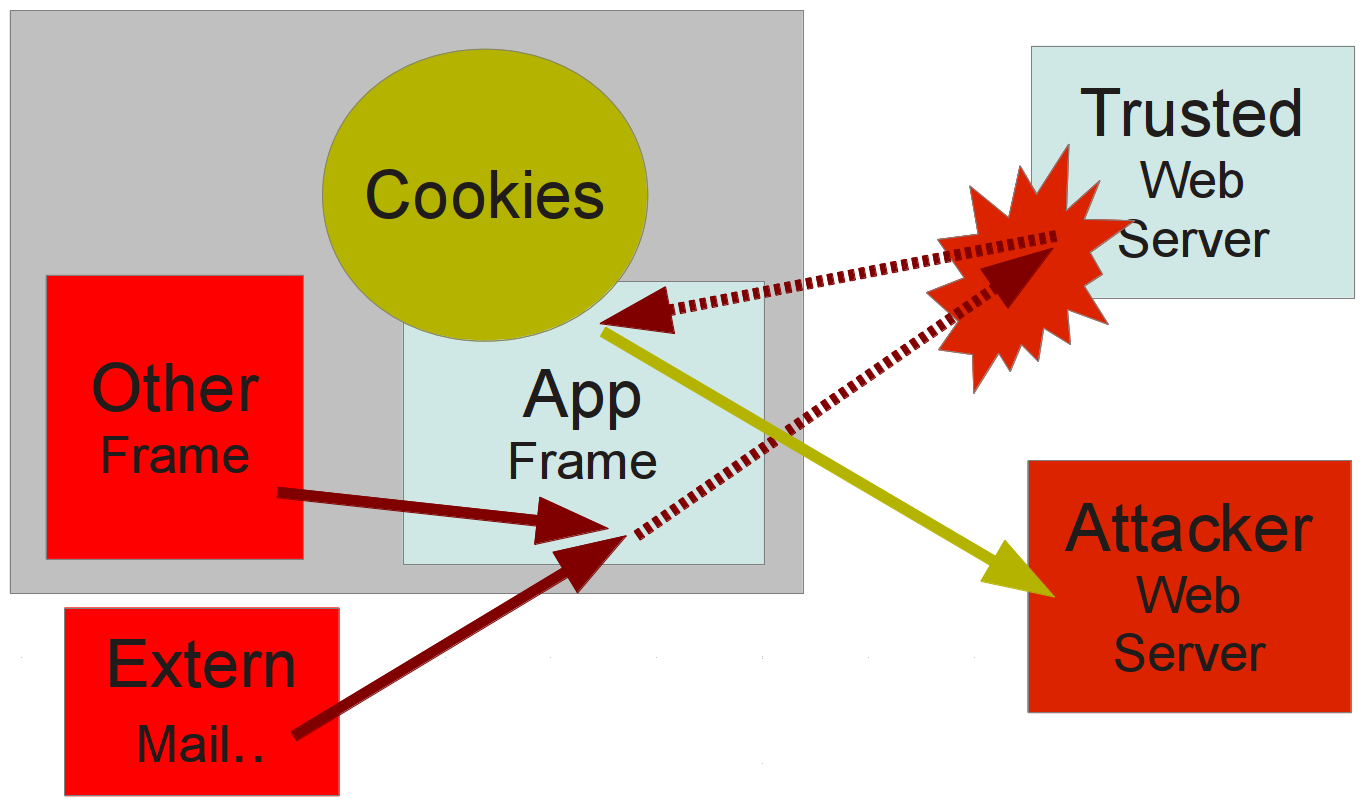
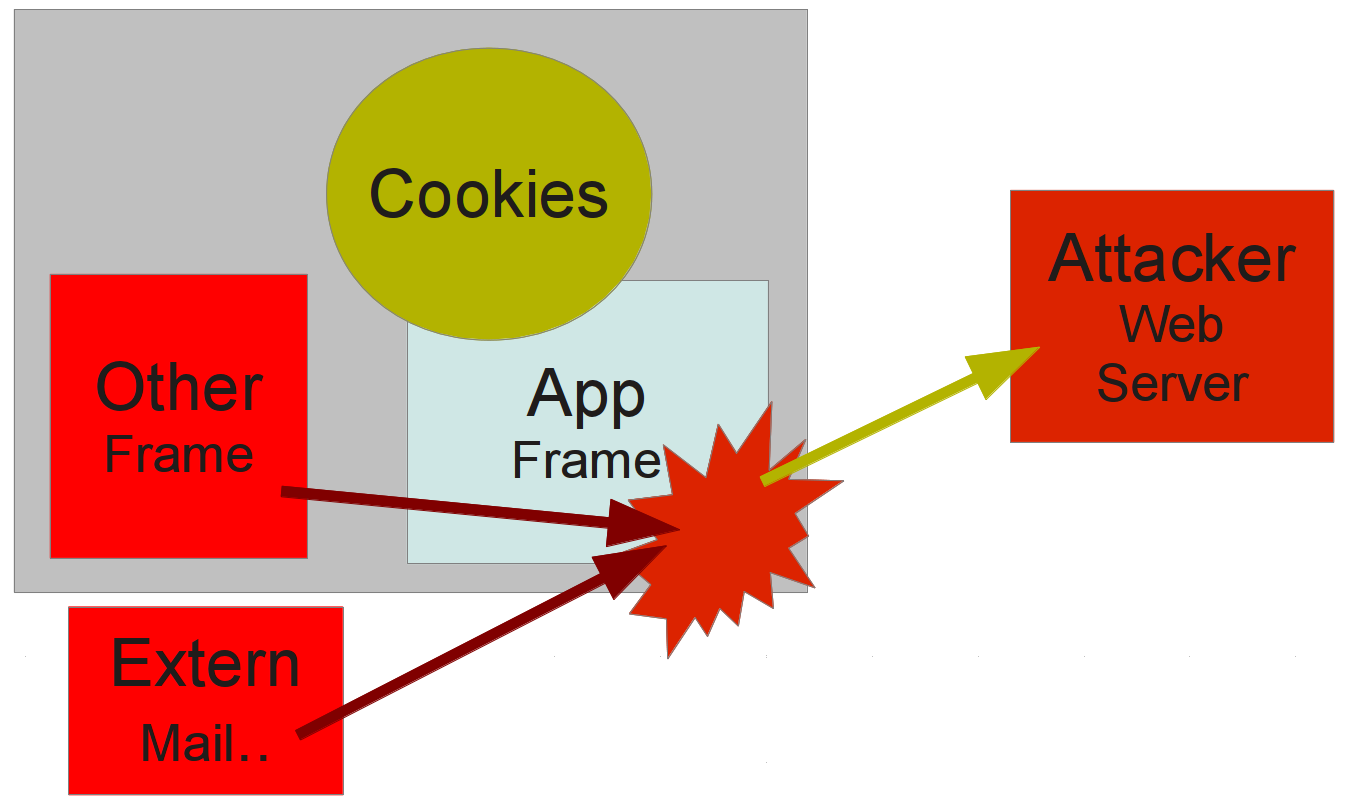
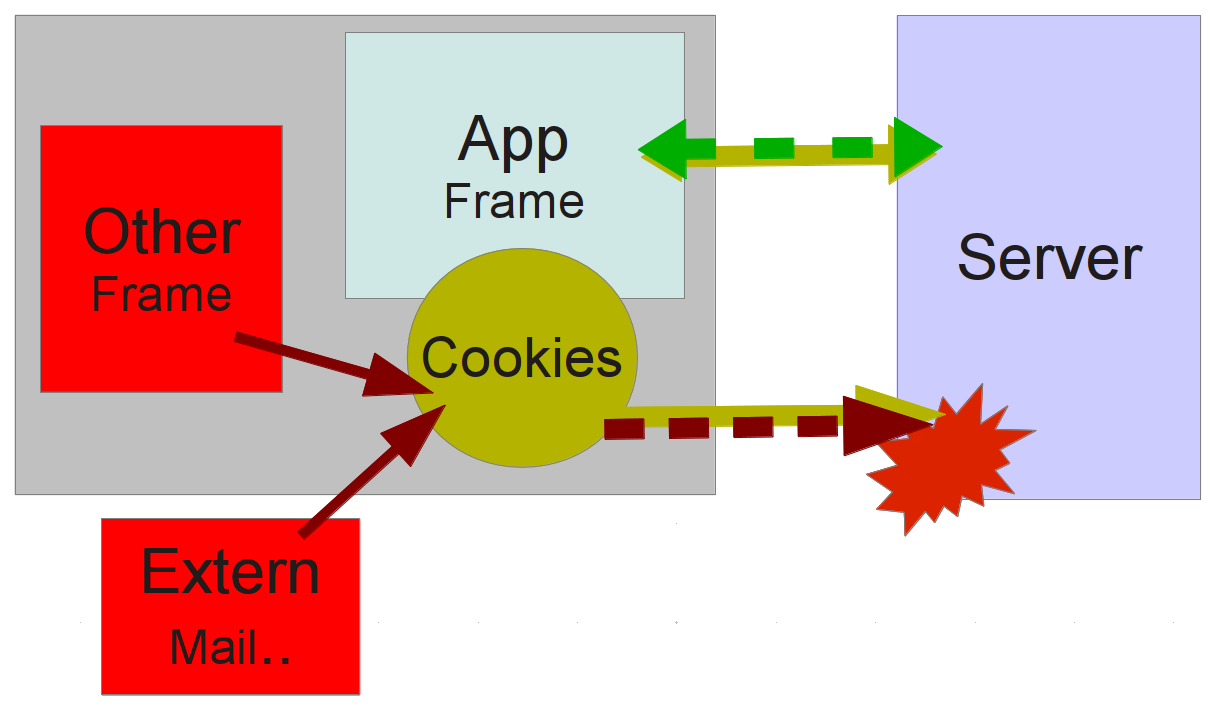
CSRF
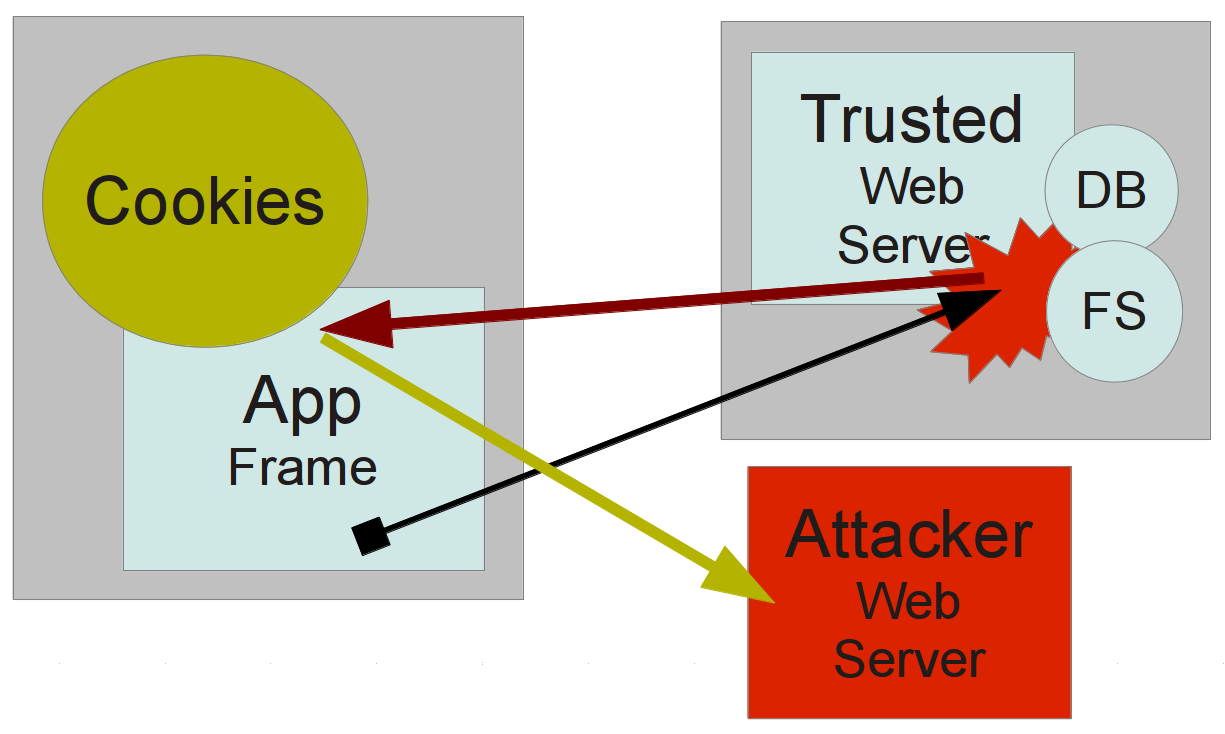
Complex Example
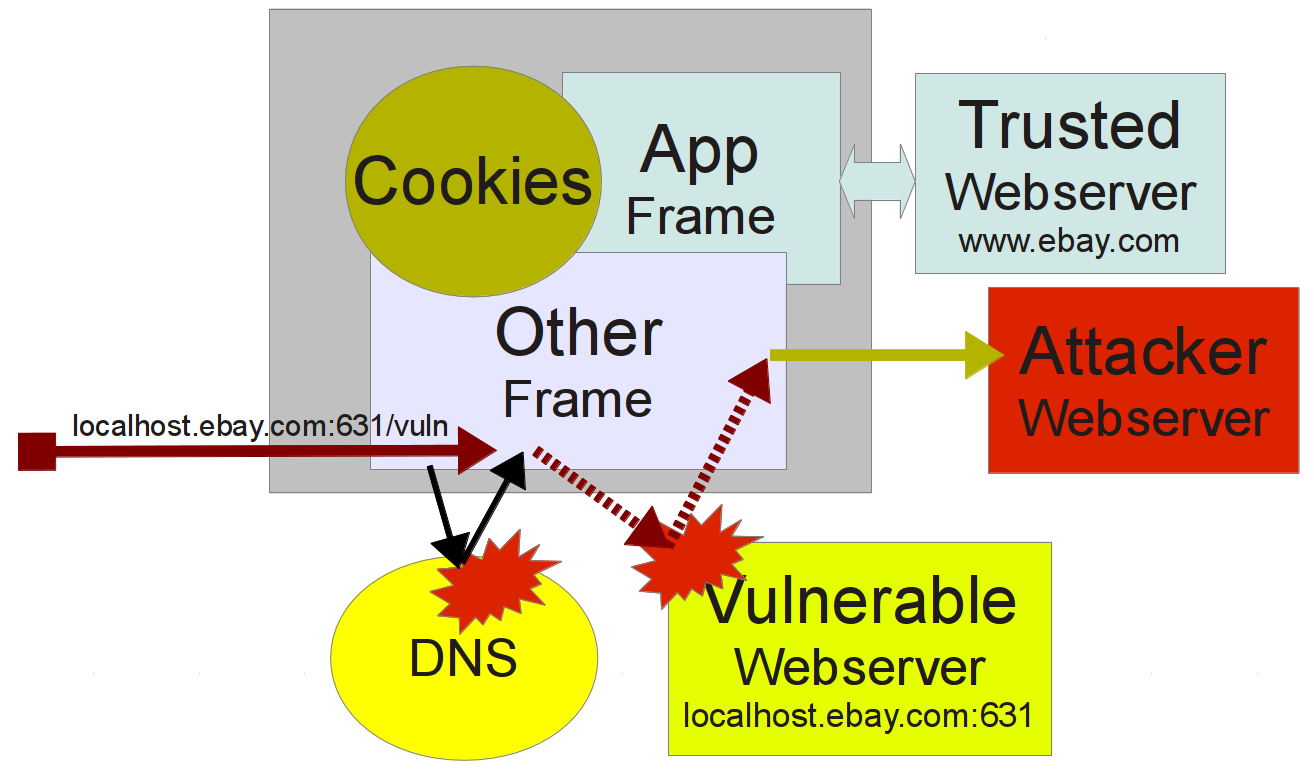
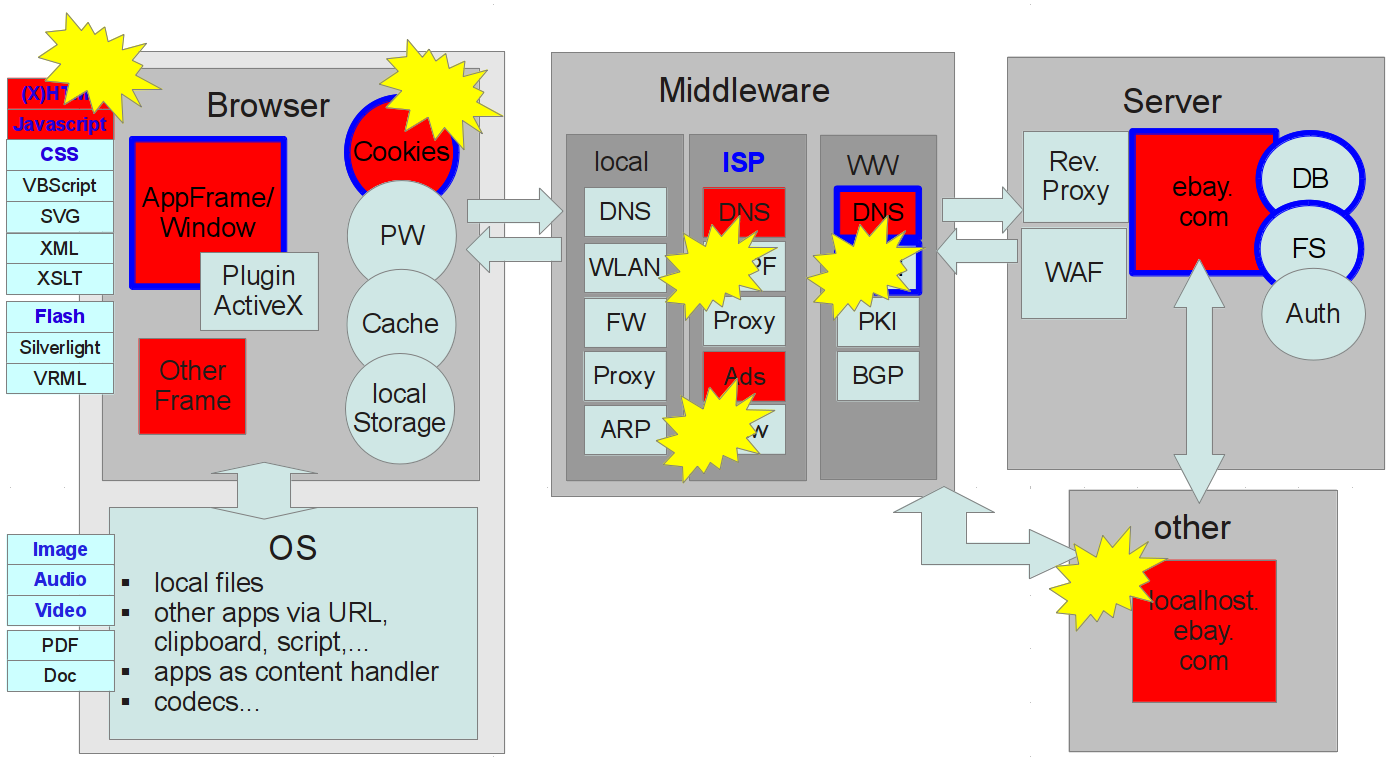
Misplaced Trust
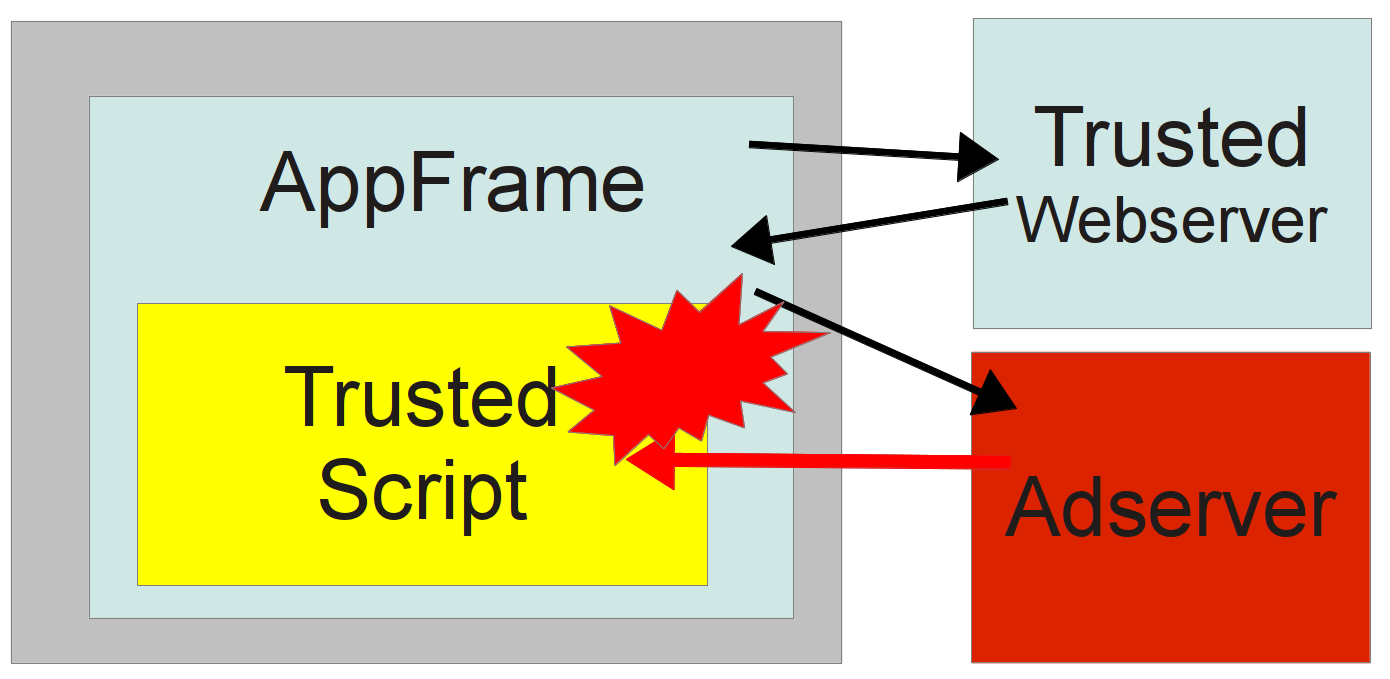
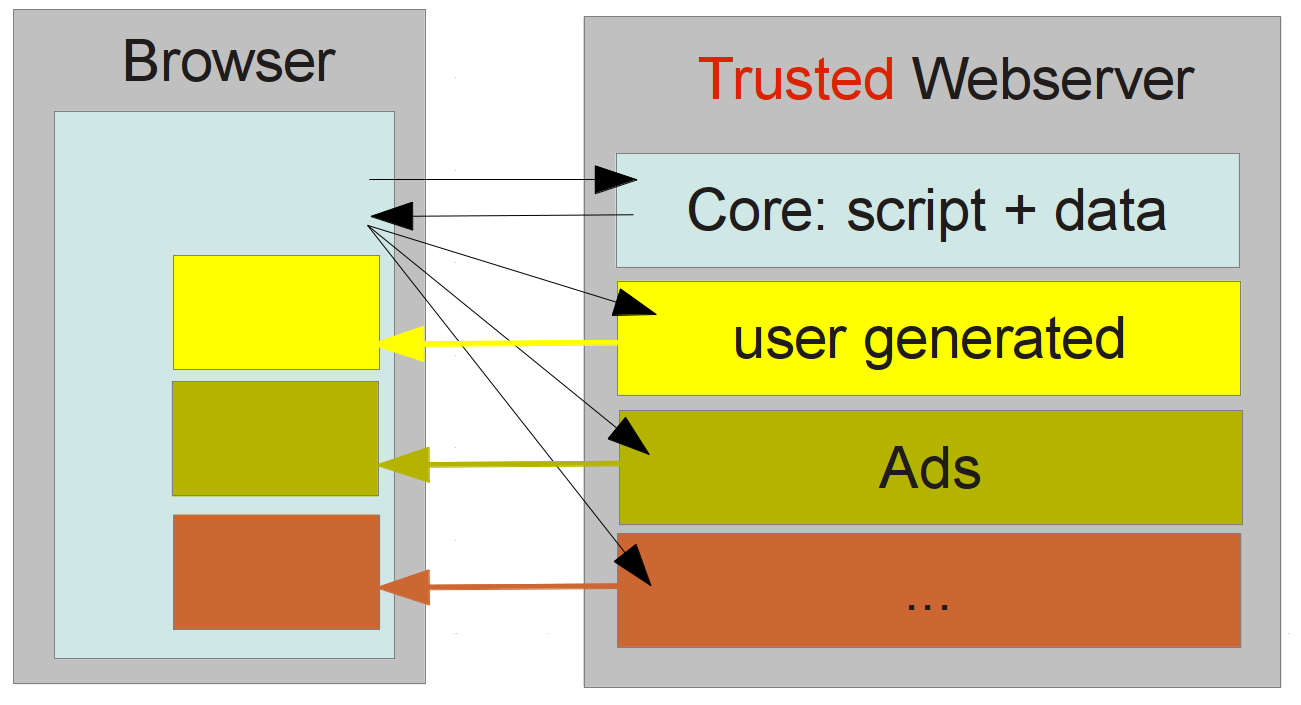
UI Redressing
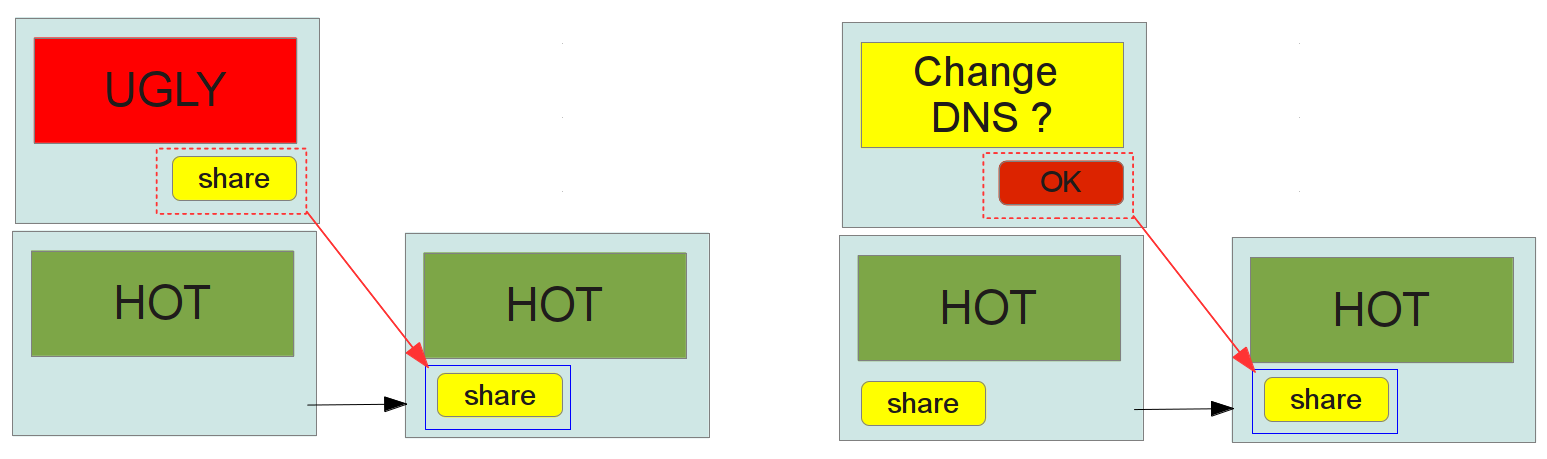
BREAK
Protection of Session
Validation
Normalization
Escaping and Encoding
Content-type
Charsets
BREAK
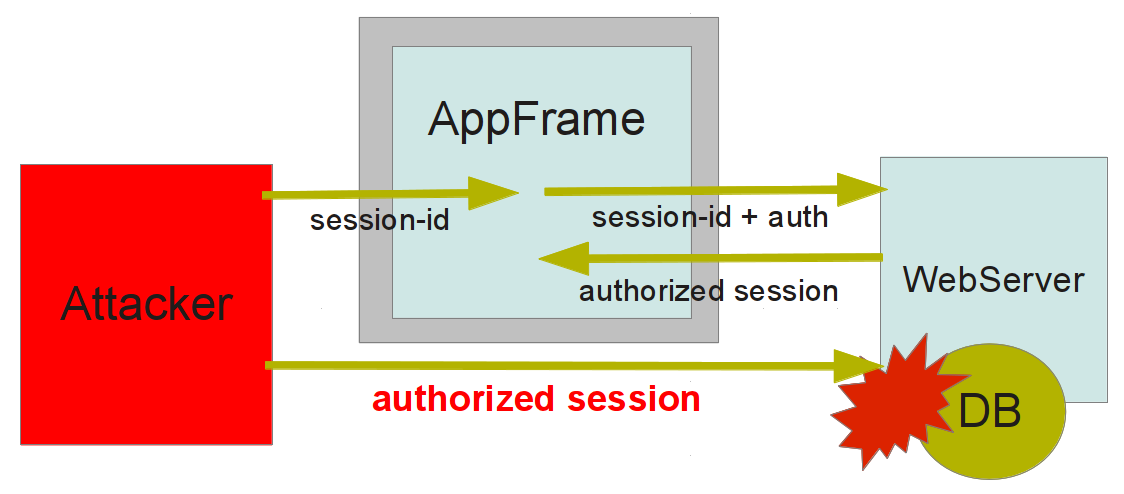
Authorization Theft
Authentication Bypass
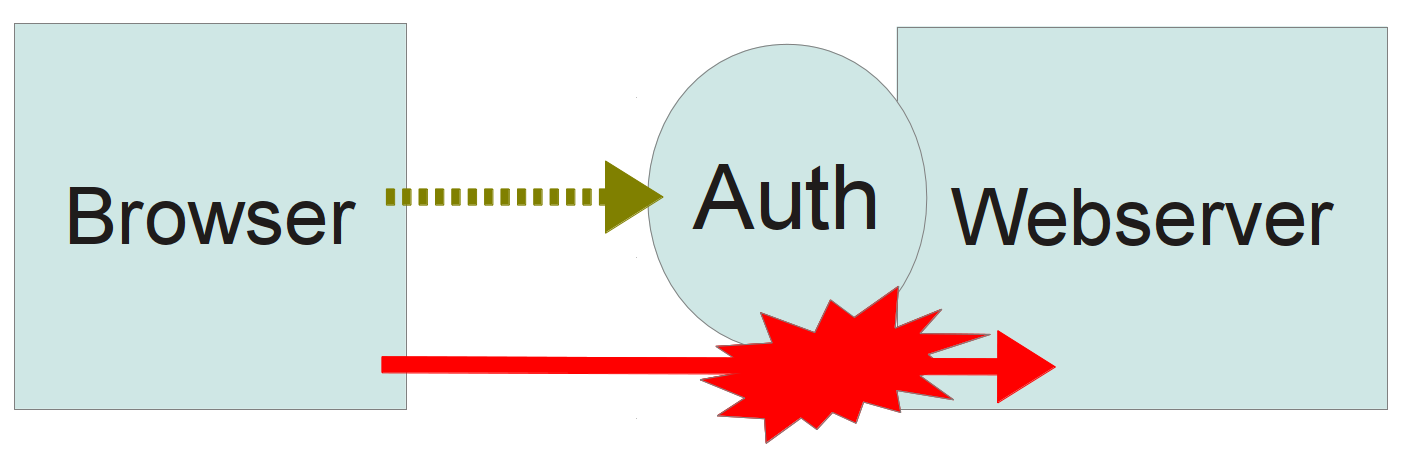
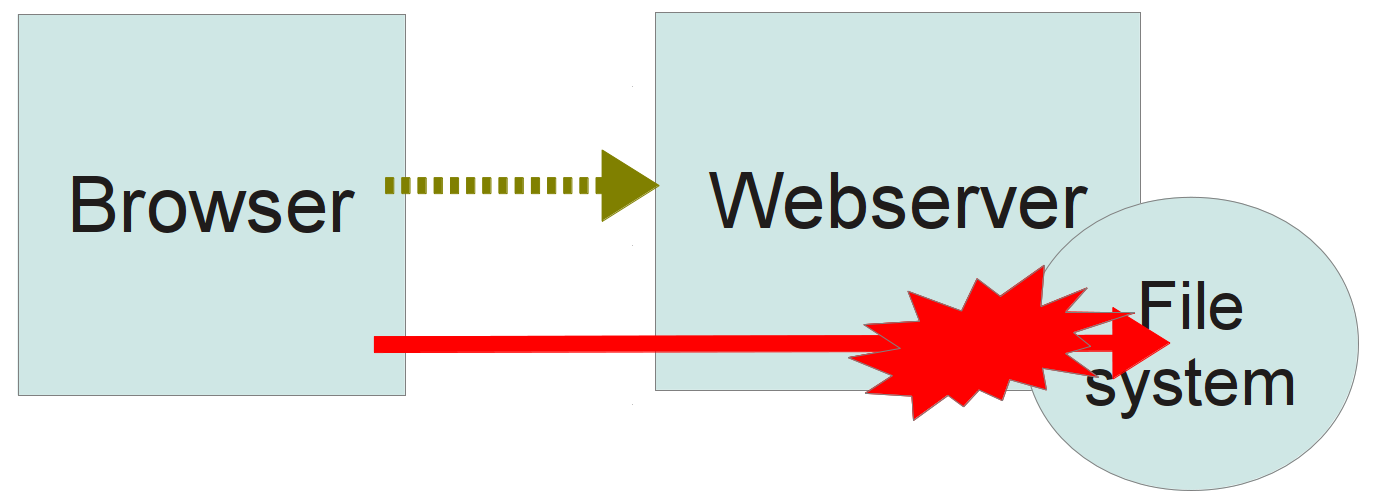
Server Permission Bypass
Network Segmentation Bypass
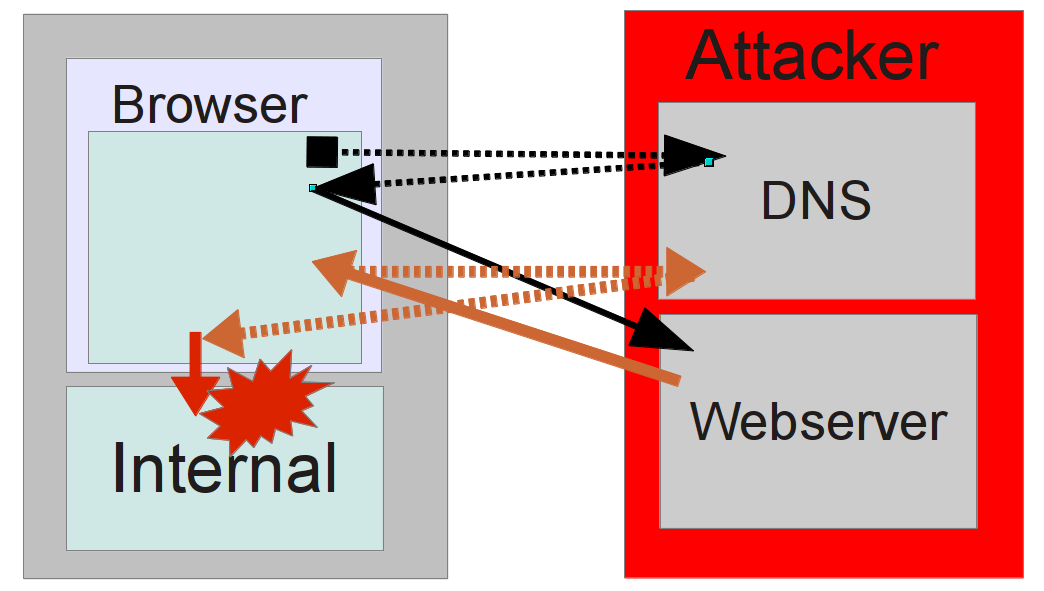
Even More Attacks
Past, Present and Future
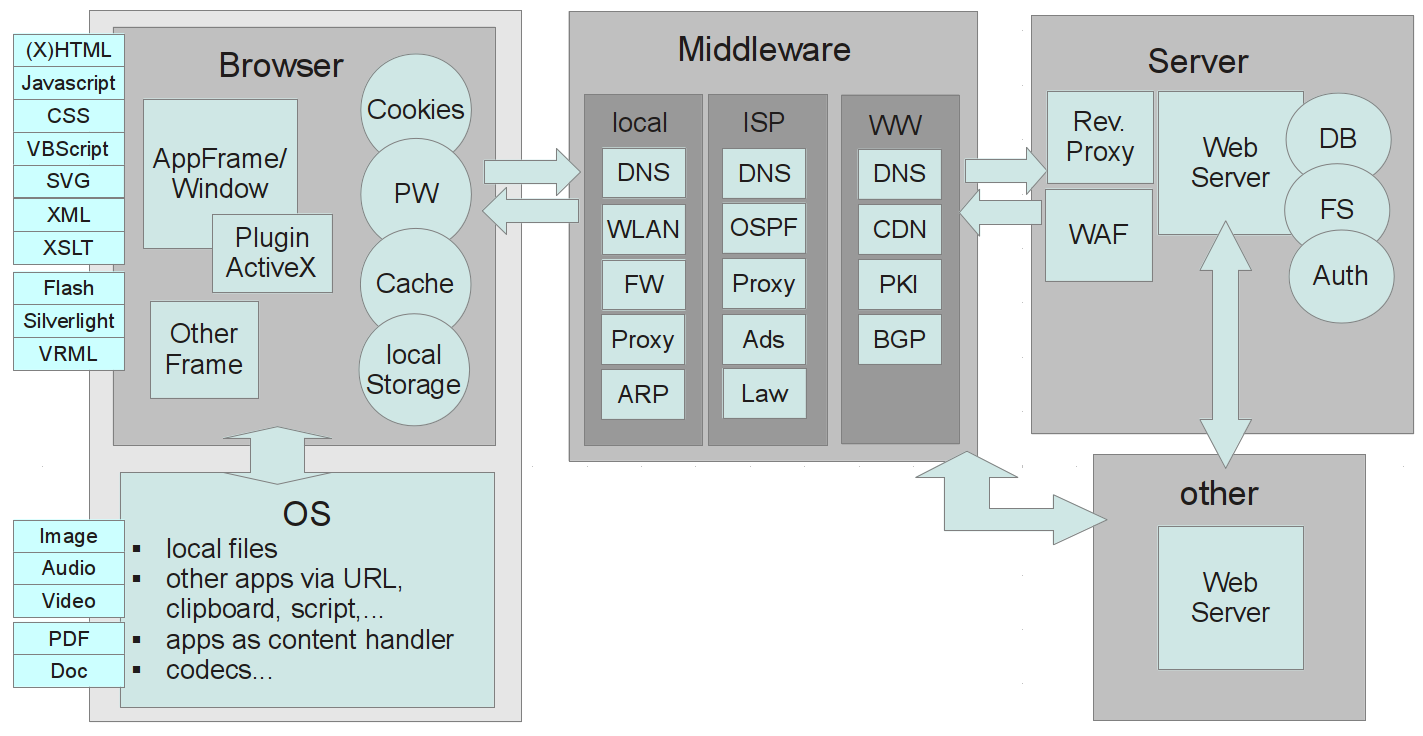
Client Side
Server Side
Resources